This blog is a transcript of the session “How to secure your precious API with API Management” by Mike Budzynski, Program Manager on API Management team at Integrate 2020.
Introduction
Last year, Gartner published a detailed whitepaper on what you need to do to protect your APIs in which they have predicted that by 2021, 90% of web-enabled applications will have more surface area for attack in the form of exposed APIs rather than the UI, up from 40% in 2019.
Also, by 2022, API abuses will move from an infrequent to the most-frequent attack vector, resulting in data breaches for enterprise web applications.
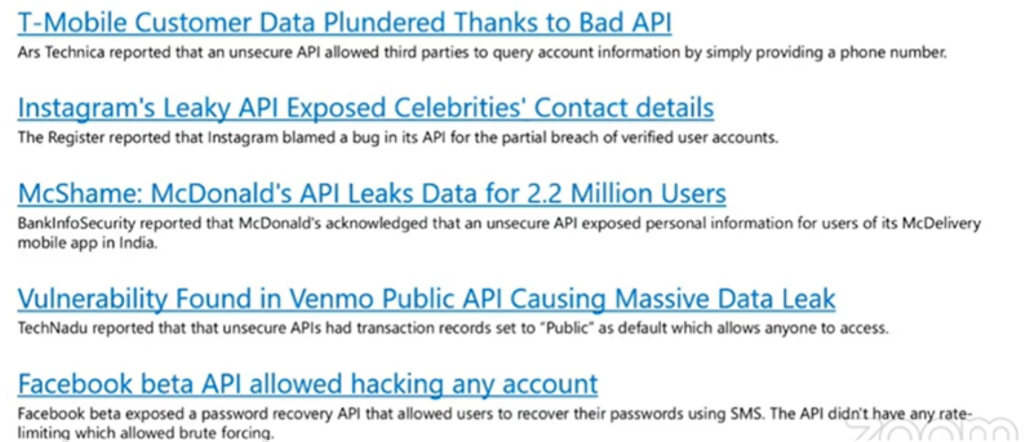
In order to have more understanding and value behind this session, you may need to look deeply on the below picture which explains a few incidents about the API attack and breaches.
Last year, an incident happened on GitHub Enterprise where one of their APIs allowed to bypass OAuth app authorization.A few things need to be observed in the above incident are:
- The bug was reported by security researched through bug bounty program
- The bug found on the API layer
- The bug was root caused and fixed in just three hours
Web app vs API security
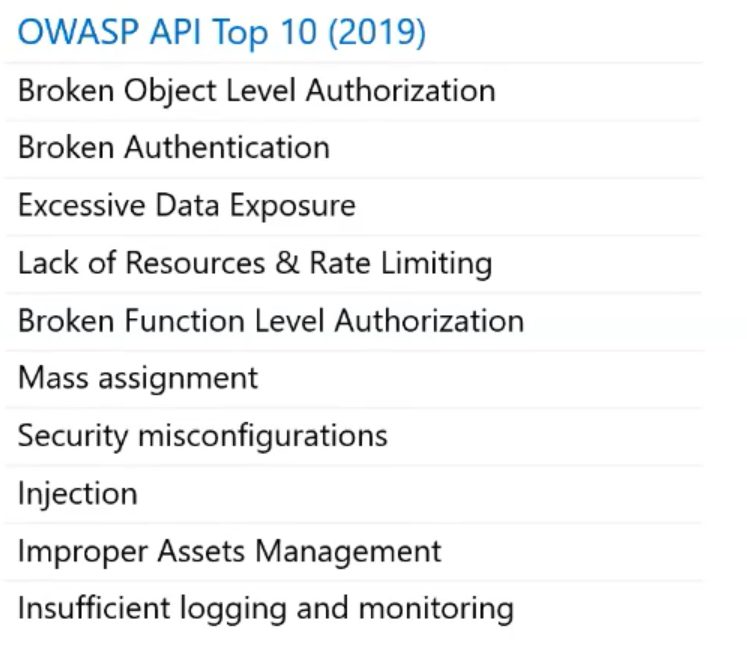
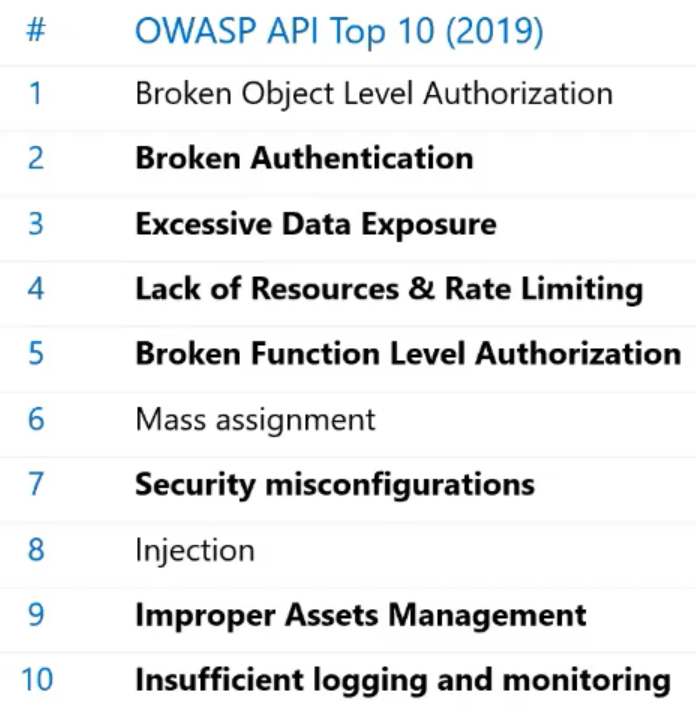
Back in 2017, OWASP community listed out the top 10 web application threads which most of the web application was prone to.

we know that web application is not only bound to the attack but also APIs do. Here is the top 10 list of API vulnerabilities that OWASP community has arrived back in 2019.
Azure API Management
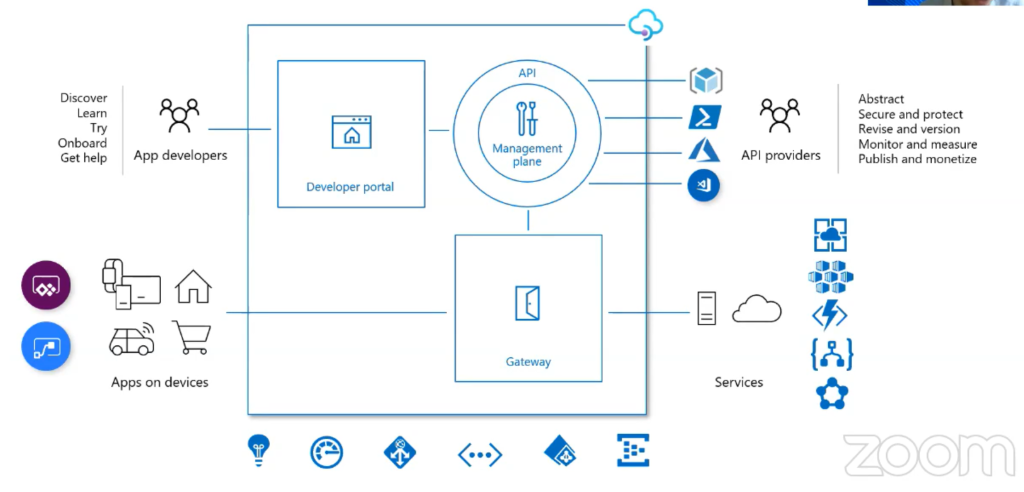
APIM instances can be updated or altered using the Management plan which can be accessed from different tools like VS Code extension, Azure portal, PowerShell, ARM templates.
Observability can be achieved by integrating API with Azure Monitor, Azure application insight and Azure Event Hubs.
Layered defence
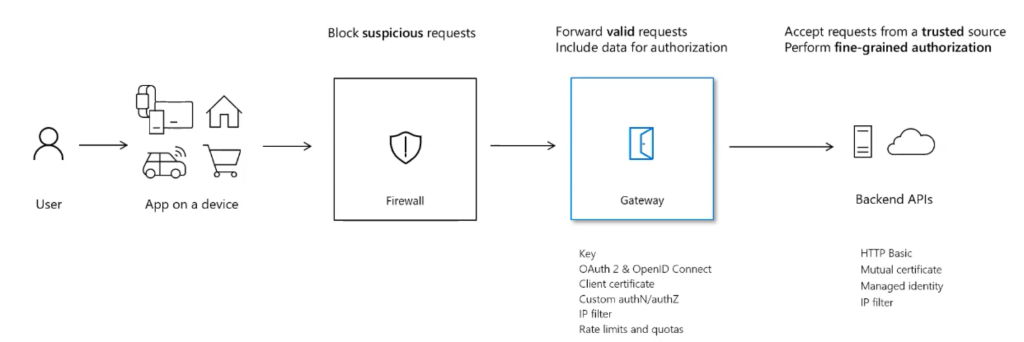
The above picture represents a typical flow of an API request. There is a user interacts with the client application/device which eventually make a call to the firewall server and subsequently to the gateway Backend APIs. In return, response goes back to all these services as well.
The Firewall blocks suspicious requests, gateway forwards valid requests include data for authorization and finally the backend APIs accept requests from a trusted source to perform fine-grained authorization.
There are some significant number of policies that fall into few categories like security, caching and more. The polices are expressed in form of XML where you can also inject C# code to extend flexibility and meet custom requirements.
Policy scope
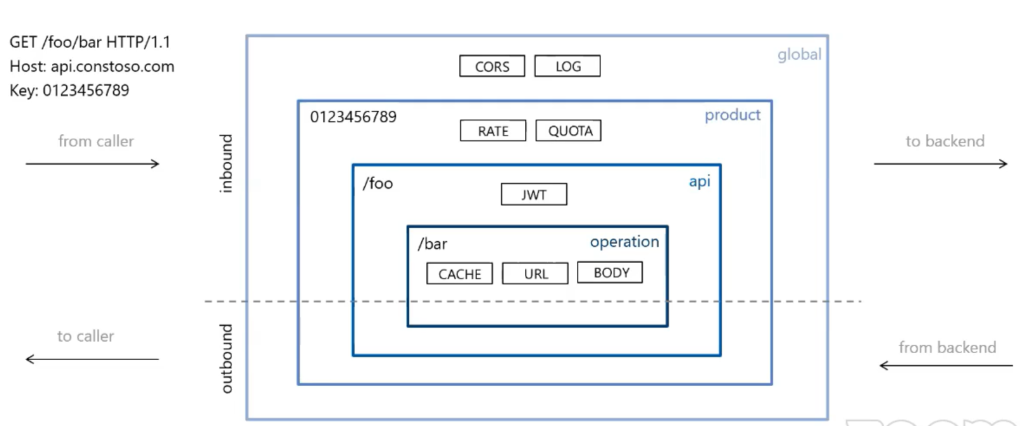
Product
Products are how APIs are surfaced to developers. Products in APIM will have one or more APIs and are configured with a title, description, and terms of use. Products can be Open or Protected.
API
Each API contains a reference to the back-end service that implements the API, and its operations map to the operations implemented by the back-end service.
Operation
Each API represents a set of operations available to developers. Operations in APIs map to the operations implemented by the back-end service. Operations in APIM are highly configurable, with control over URL mapping, query and path parameters, request and response content, and operation response caching. Rate limits, quotas, and IP restriction policies can also be implemented at the API or individual operation level.
API management to the rescues
Below is the list of marked threads from OWASP community that APIM can rescue the users
Improper assets management
It is not recommended to expose specific backend resources limit HTTP methods on exposed resources deprecated APIs or versions. APIM allows you to manage various versions under the hood.
Security misconfigurations
Security misconfigurations are one the major threat for API. The common ways to prevent is to enforce HTTPS traffic for your APIs or in other words, disable HTTP traffic for your APIs. And manage protocols in cipher and always restrict cross-origin resource sharing.

DEMO – Disabling HTTP Endpoint
When you normally call your API endpoint in HTTP or in HTTPS it works for both the scenarios. But we need to restrict the HTTP call for our API. In order to do this in the Azure portal move to the API Management section in the Azure portal and select the APIs tab.
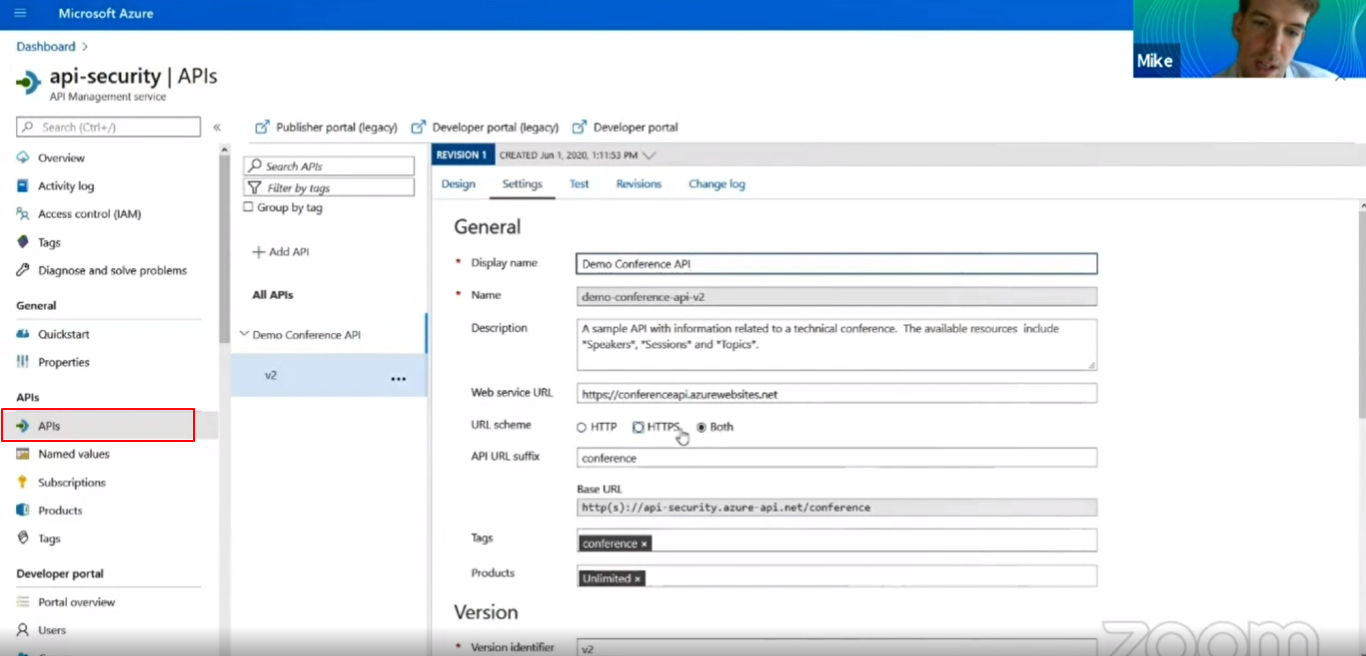
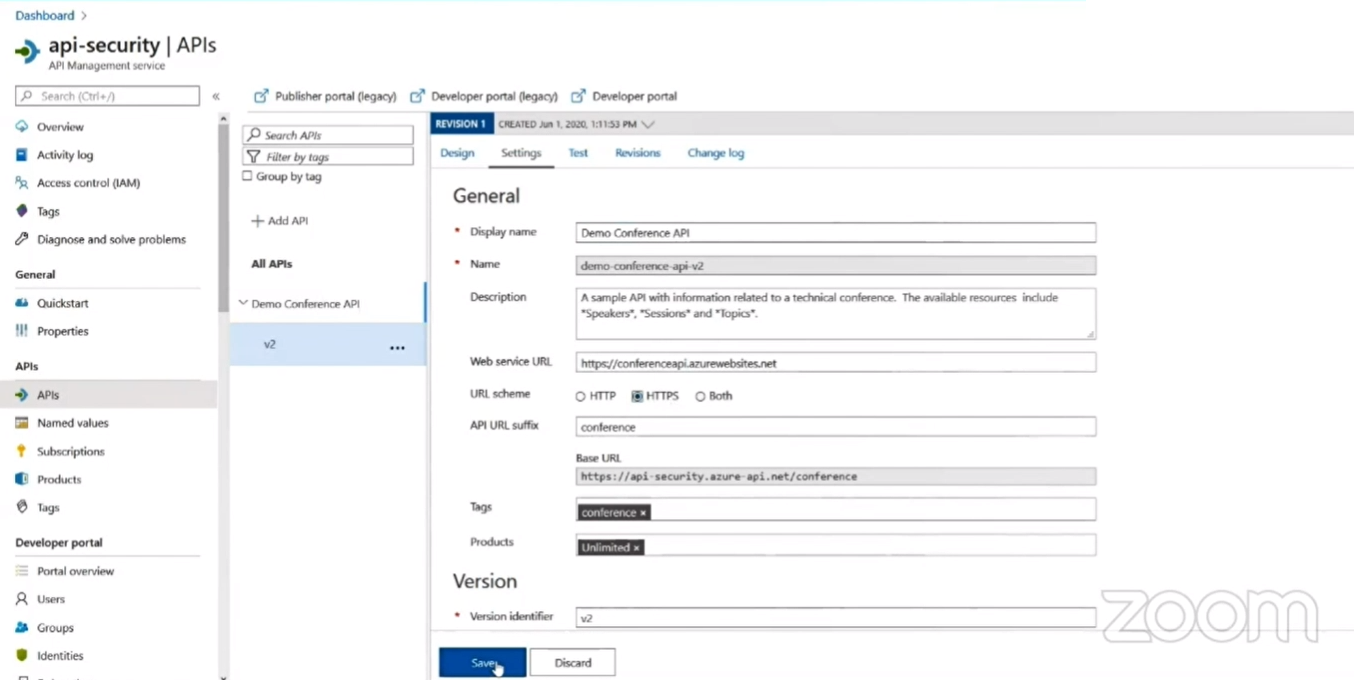
In the APIs tab, in General you can see an URL Scheme. By default, your API will allow both the request (HTTP, HTTPS). Now select the HTTPS option and hit the save button.
And now when we try calling our API in HTTP method, it will fail.
DEMO – Managing Ciphers in Azure Portal
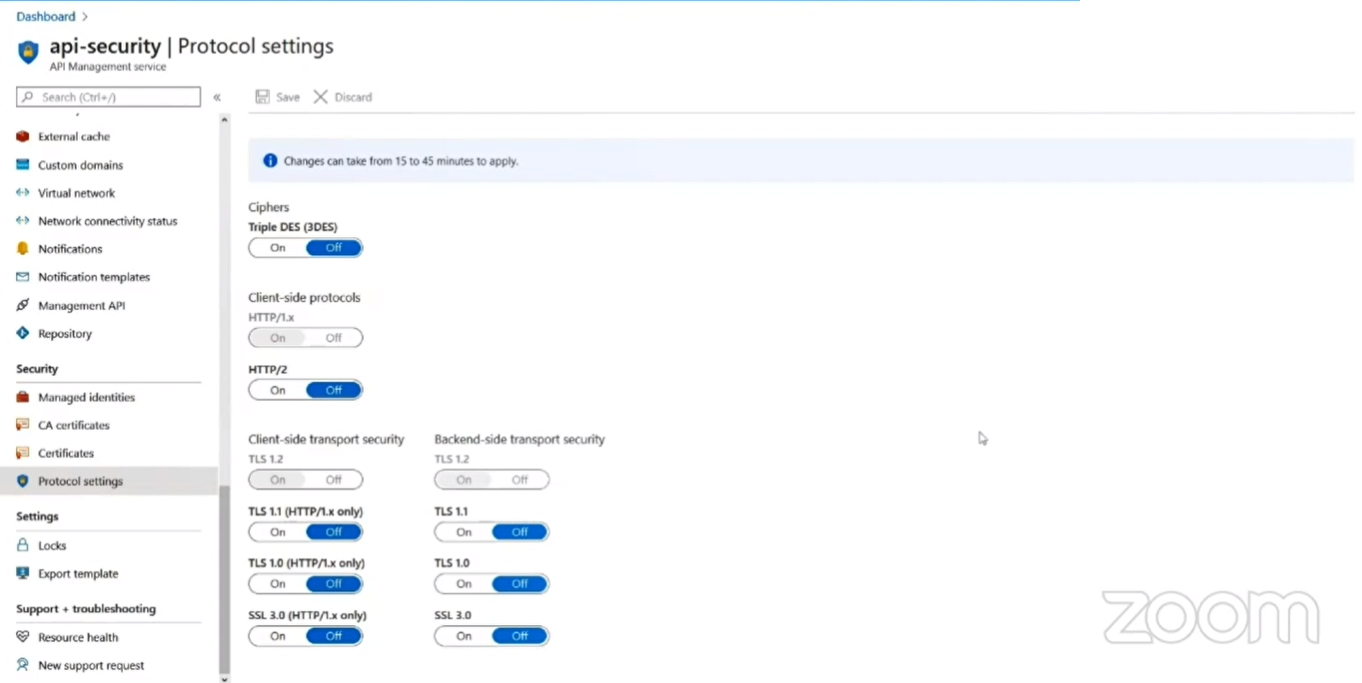
In Azure portal move to the API Management section and select the Protocol settings. Here you will have the option to manage some Ciphers in your API. But before enabling any of the cipher beware of the Cipher as some Ciphers are vulnerable.
DEMO – Cross-origin resource sharing
In order to prevent Cross-origin resource sharing, move to API Management in Azure portal and select the APIs tab and from ALL OPERATIONS click on the Add policy button. Now from the list of policies available select the Allow cross-origin resource sharing and in the Allowed headers, Exposed headers put a *(star) which will act as the default value and allows all the values and select the save button.
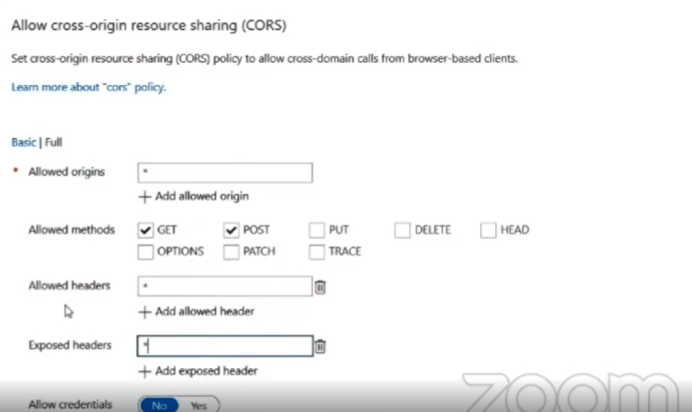
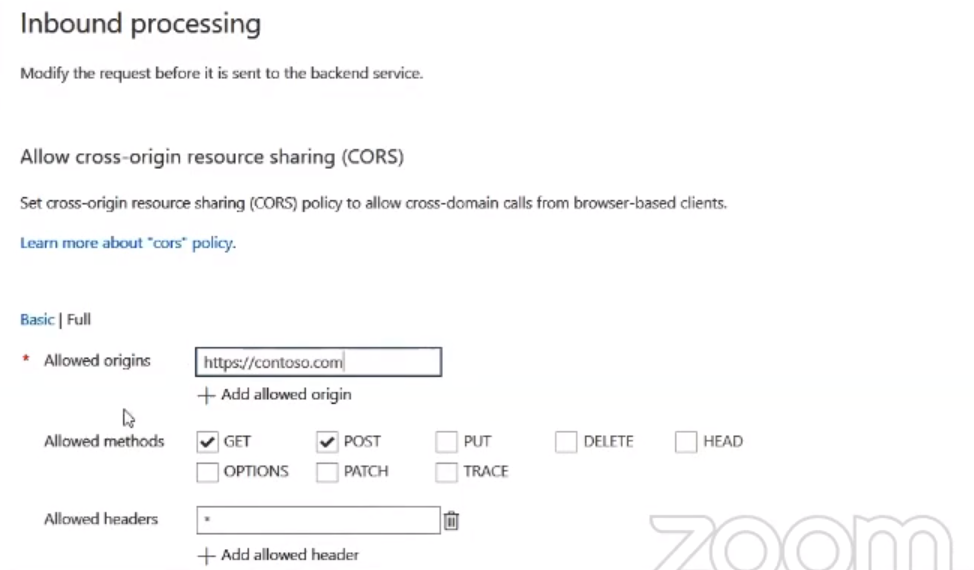
But one of the drawbacks of this method is that, even the malicious website can access our API. To prevent this, we need to put the precis website link in the Allowed Origins that needs to access our API.
Excessive data exposure
Excessive data exposure is another common threat in the APIs. In this case some of the unwanted data will also be exposed while accessing our API. To prevent the exposure of excessive data you can
- Filter or mask sensitive data in the response of our API
- Standardize error messages ahead of time
For example, in a transaction if our Card details are stored in the header of our API then it will be exposed to the websites who request our API.
DEMO – How to prevent Excessive data exposure
Move to the Azure Portal and inside API Management select the respected API and call our API, the response will be in a JSON format and in that there will be a section called Request-Context
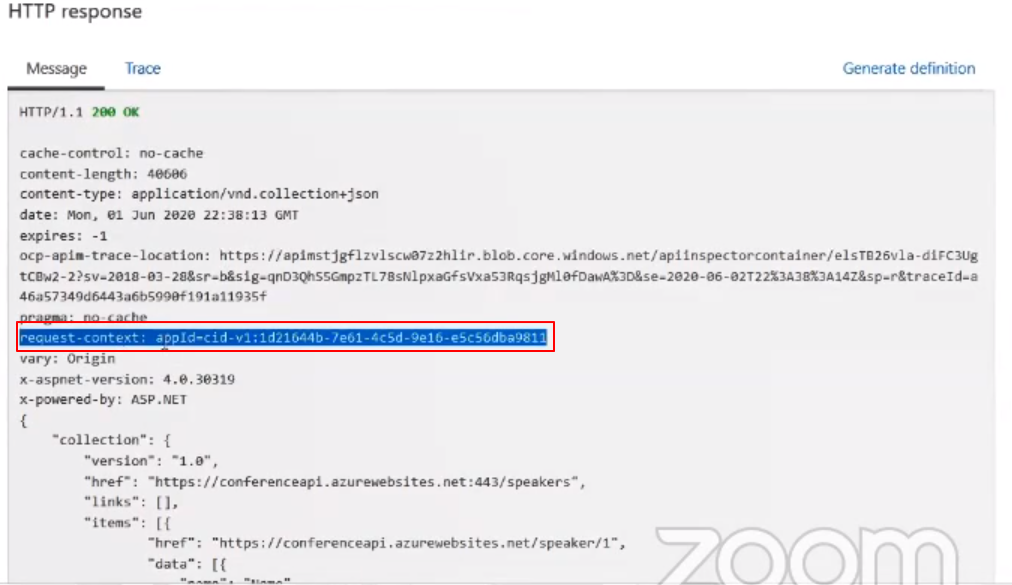
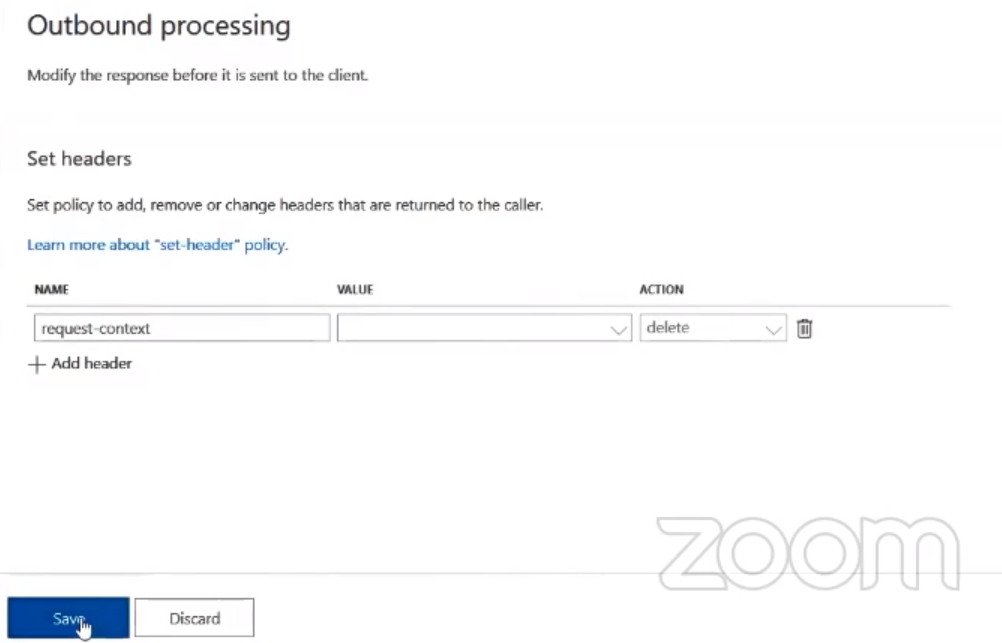
This should not be exposed to the outside world. So now to prevent it move to the API Management section in the Azure portal and select add policy from the All operation tab. Select the Outbound Processing and add the request-Content parameter and in the action, field choose to delete and save.
Broken Authentication, Authorization
This is one of the most complex topics in the API Management in any organisation. There will be a team building the API and others use it. So, while developing the API most of the requests and parameters are misconfigured. So the following are some secured ways to develop APIs
- API Keys
- JWT Tokens
- Client certificates
- Custom authN and authZ services
Custom Authentication and Authorization is one of the most advanced ways

In the API Management policies, there is a separate policy for the JWT token which can be used to create a JWT token for our API.
Security-first API Program
In order to maintain high security for your APIs, the following are some tips
- Bug bounty program
- Dedicated security team
- Enforced through DevOps, Azure Policy
API Management to the rescue

Conclusion
API security is one of the top concerns in embracing API strategies. In this session, you will get to know the common API security flaws, learn how to protect against them, and explore mitigation options if the worst happens.
Closing Notes – Saravana
Saravana Kumar, CEO of Kovai.co thanked all the Attendees of INTEGRATE2020 for attending the sessions. He also thanked all the team members who worked at the background for orchestrating this event. He even thanked all the Speakers of the event who worked despite different time zones and made this event even more special. Kovai.co once again proved its dedication with regards to community activities and showed how we give back knowledge to the society. He also talked about the current situation and intimated all to be safe. Finally, Saravana informed the attendees about the survey forms which could helps kovai.co to build this event stronger next year.