This Blog is the readable version of one of the exclusive sessions of the Integrate 2020, which is “Azure Governance and Security for Enterprise Integration under the hood” by well-known Microsoft MVP – Nino Crudele.
To give an overview of this session, it was more on Security and governance of the Enterprise Integrations. It covered a lot of hacking methodologies by hackers and tools in Azure to prevent from them all. This session was focused on three areas that are mentioned below
- About Hacking and Hackers
- Real-world hacking insights
- Ways to secure Azure
Nino started his session by introducing himself to the attendees. He is a freelance architect and a Certified Ethical Hacker. His area of focus is on Azure Governance and Security. He is also a Microsoft MVP for 14 Years since 2006.
Now let us start with a detailed note on the topics covered in the session.
Hacking and Hackers
To Beat a Hacker, you must think like a Hacker
Nino began his session with the above quote and showed some common profiles of the hackers
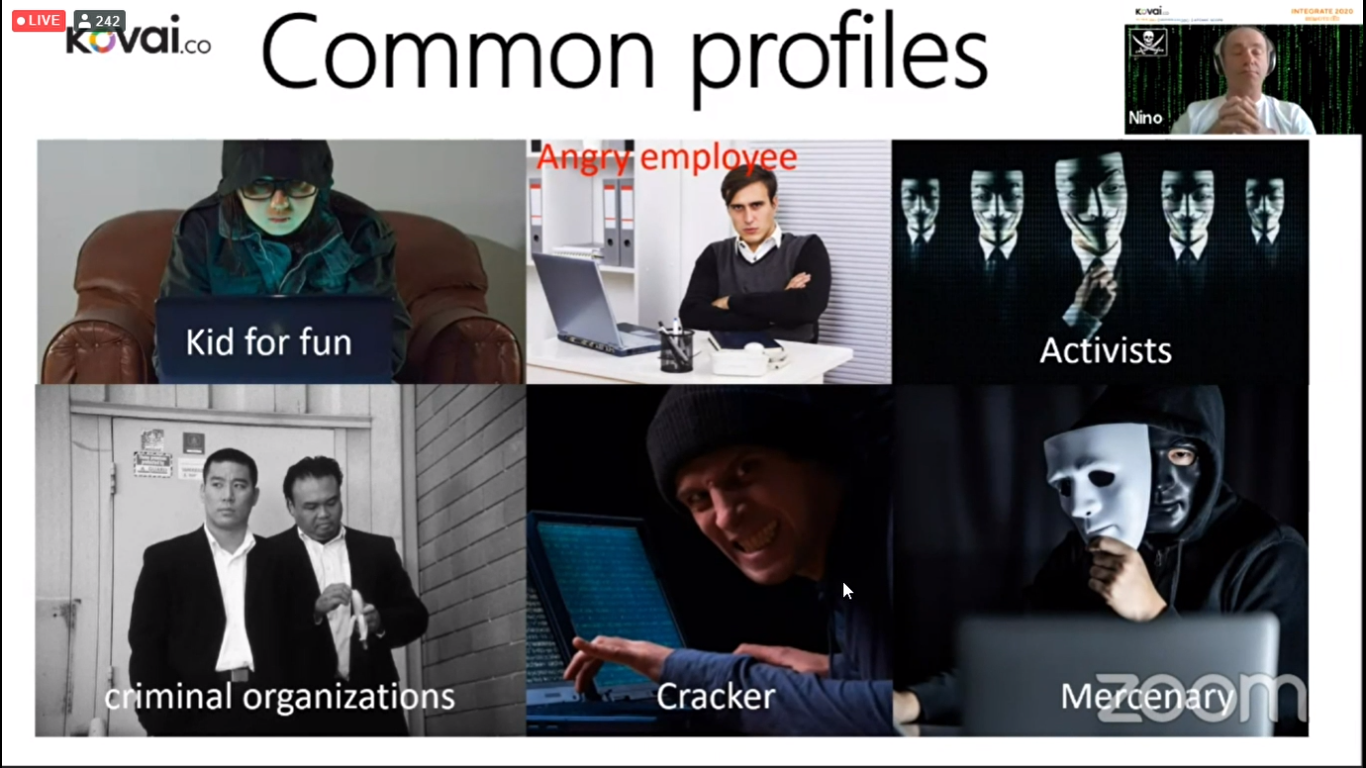
He explained how a hacker of other organizations can easily hack your organization information by just getting into a company as an employee and slowly get all the information and secret that are needed.
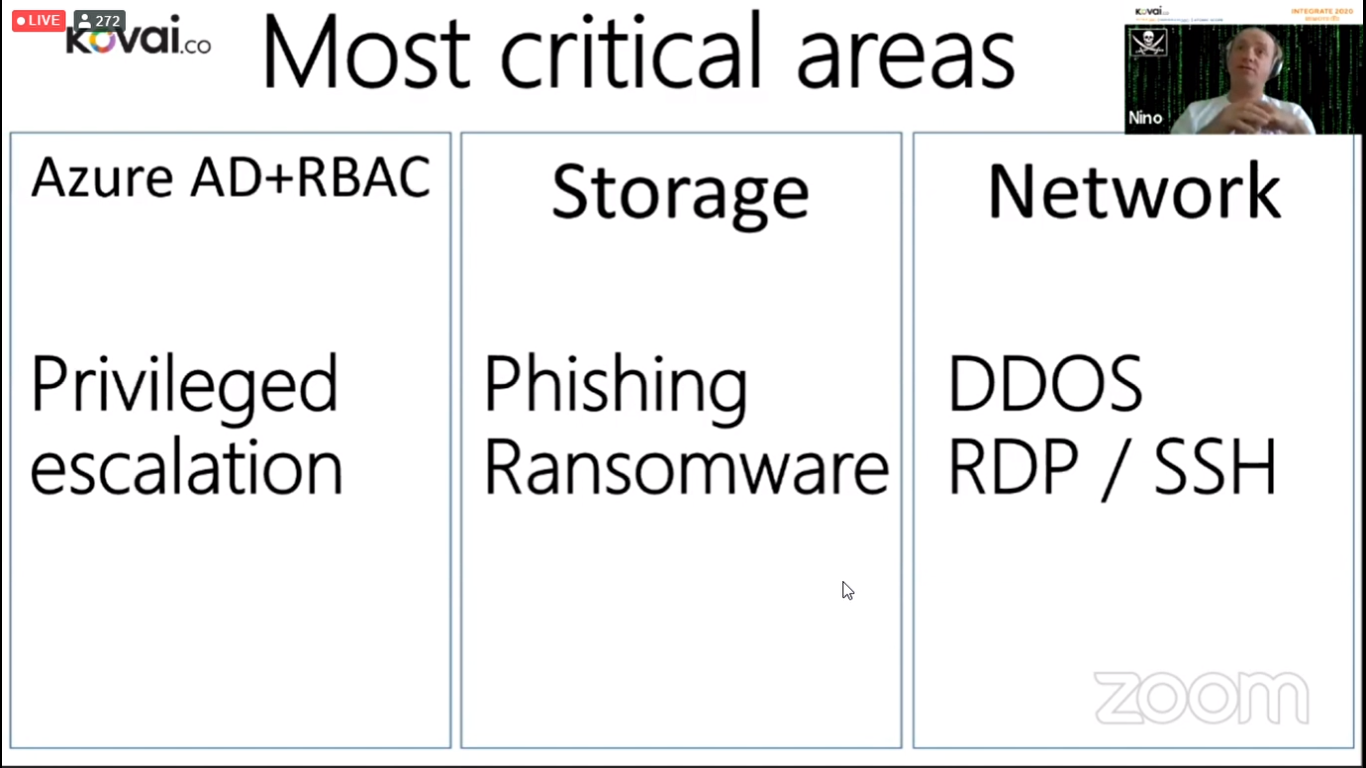
Most Critical Areas
From his experience, he listed the three critical areas where most of the attacks on Azure would happen,
- Azure Active Directory
- Storage
- Network
And Below are some attacks that happen on respective areas
- Azure Active Directory – Privileged Escalation
- Storage – Phishing/Ransomware
- Network – DDOS and RDP/SSH
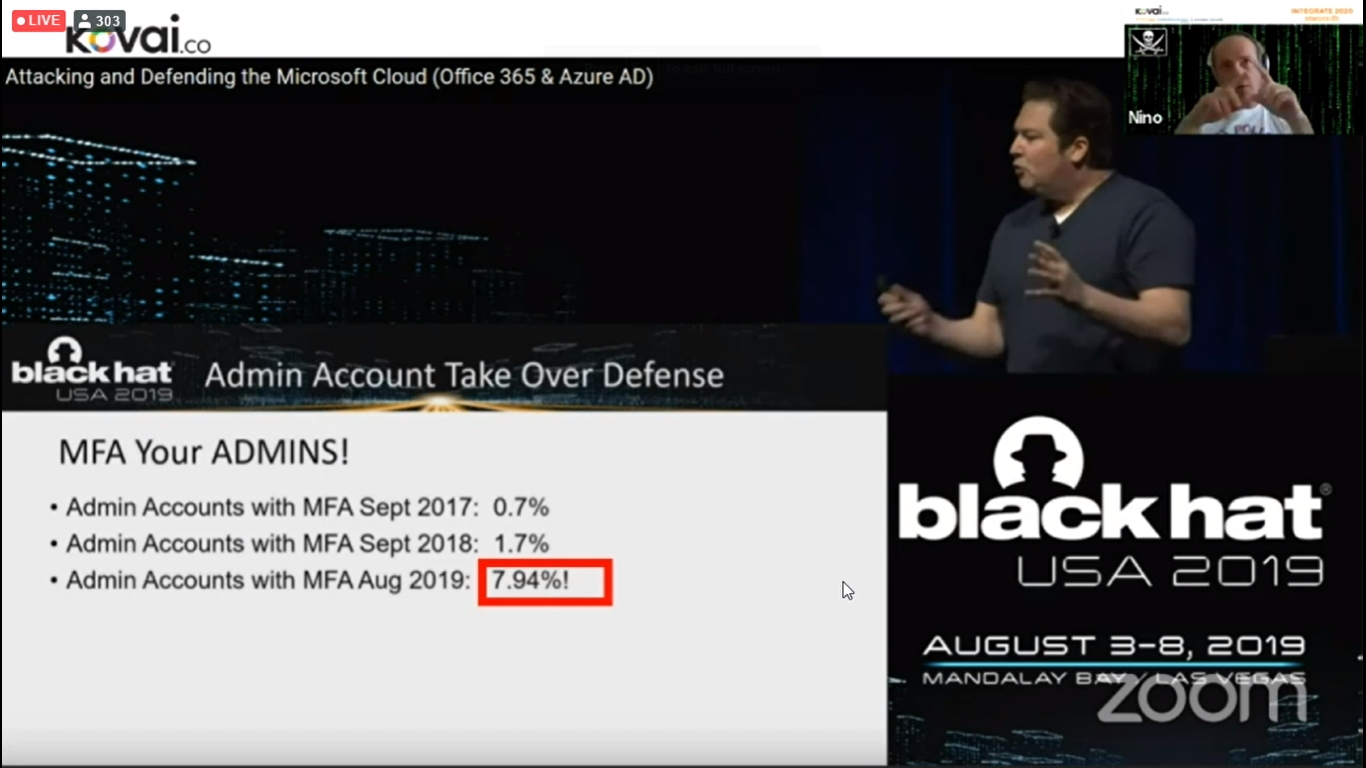
He mentioned some common challenges in being a global admin. Global admin will have access to all the Management groups, Subscriptions, and tenant. So, it is very important to enable services like Multi-factor Authentication (MFA). He also gave statics on some real-world numbers of people using MFA in different years.
Tools
He started this section with some physical hacking tools like duplicate keys and WIFI hacking tools connected with raspberry pi etc.,
He also introduced some software tools to get insights about hacking that were happening at the time of the session.
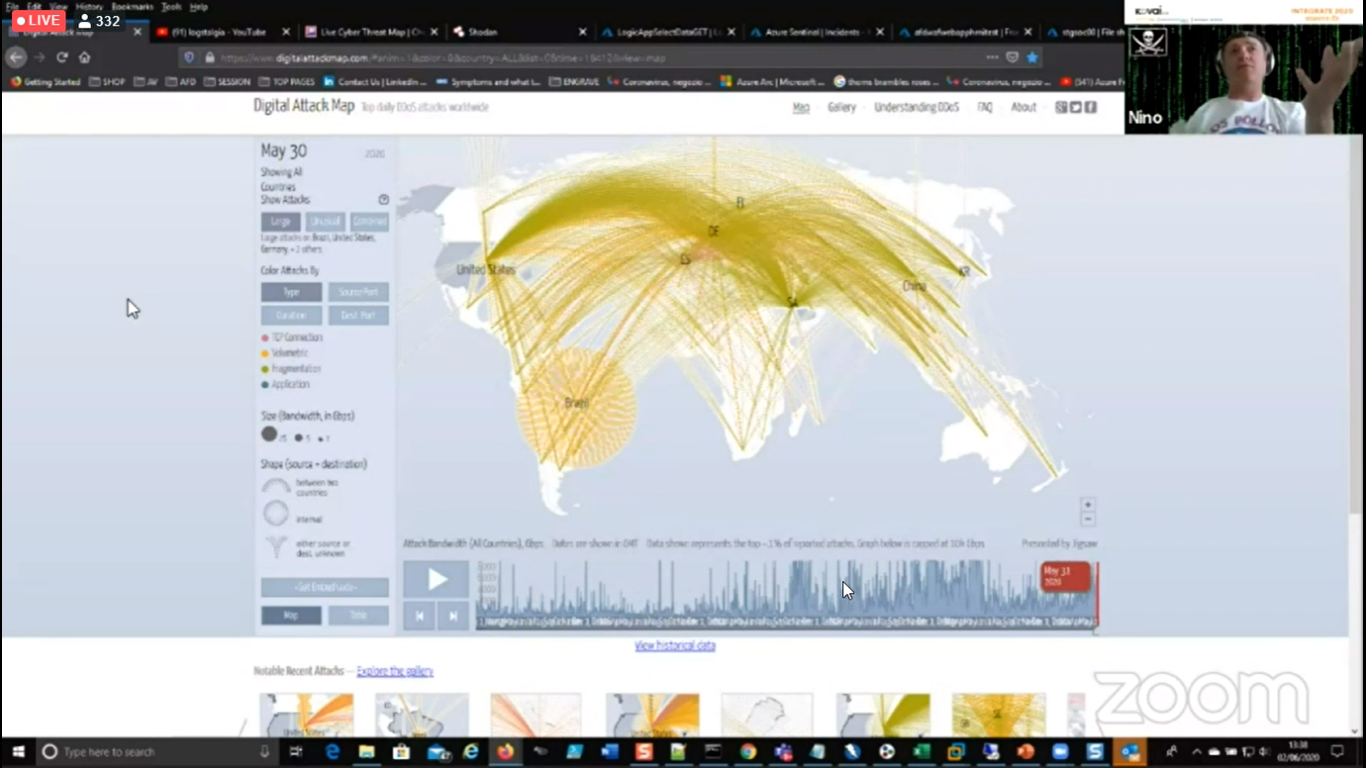
1.) Digital Attack Map – To know about DDOS attack that is happening at present
2.) Cyberthreat Kaspersky- Real-time hacking information tool
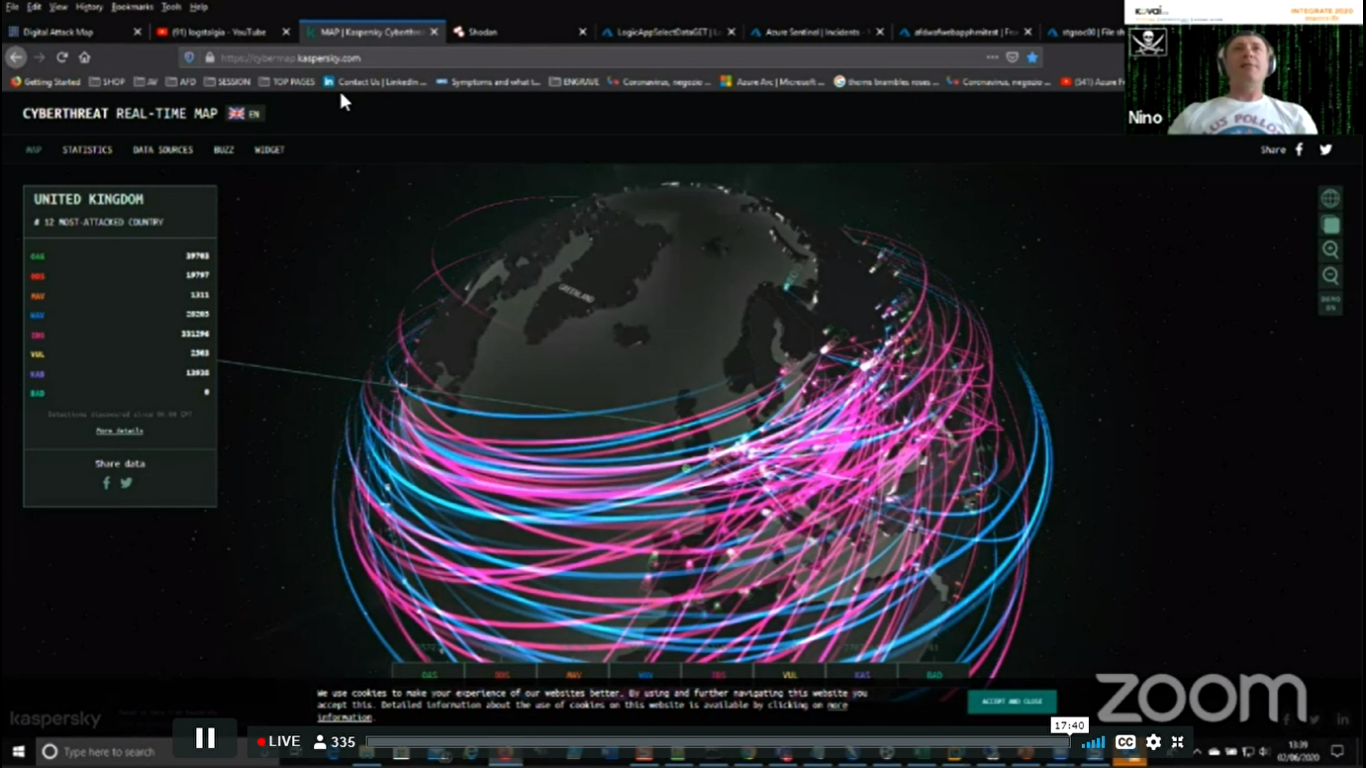
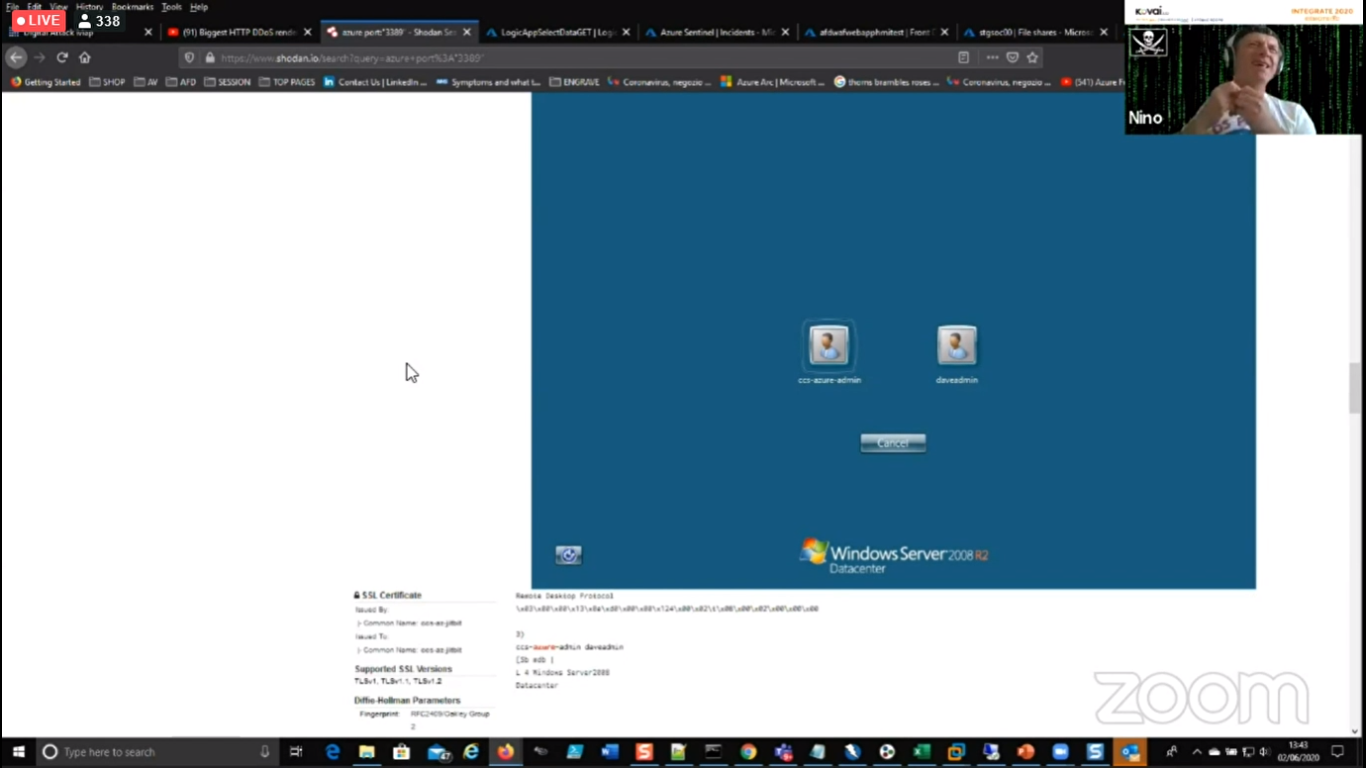
3.) Shodan – tool to know information about virtual machine data
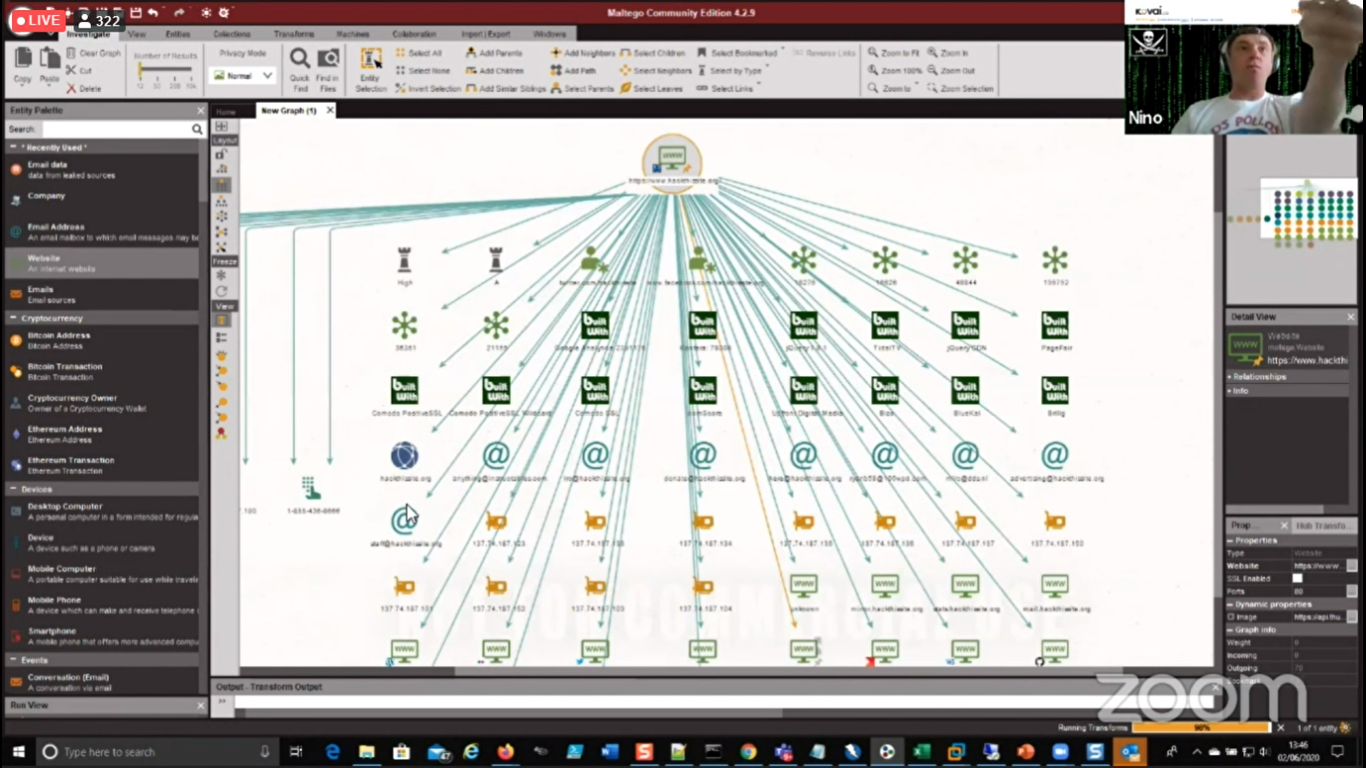
He also showed a tool named Maltego which is works and explains deeper on what is the system that relates to the specified system. From this tool, hackers can easily get the necessary information like what kind of tools an organization is using, who is the manager and who is admin, and what are the naming conventions being followed in an organization that are very much useful for hackers.
He also showed a tool named Maltego which is works and explains deeper on what is the system that relates to the specified system. From this tool, hackers can easily get the necessary information like what kind of tools an organization is using, who is the manager and who is admin, and what are the naming conventions being followed in an organization that is very much useful for hackers.
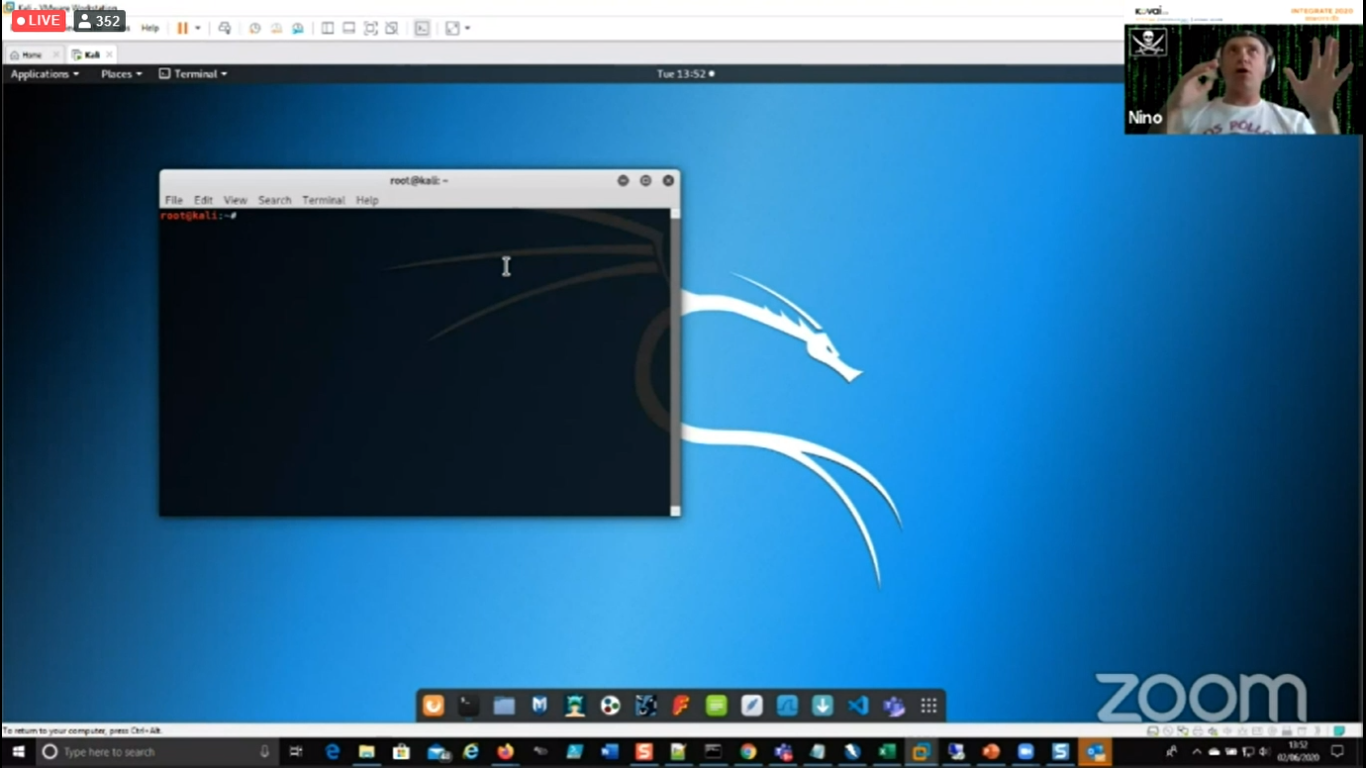
“Even though Azure Sentinel prevents and detects the attack. It will get to see the last node from where the attack has come. It cannot easily track the source IP address of the attacker. So, it is even more important to keep our data more secure” he advised.
Conclusion
Finally, it was a Q&A session. Nino covered the session very lively and gave some real-world insights and advice regarding the security of our Azure resources. Thanks for his wonderful session that covered everything related to security and governance.
This is short coverage of the session and Stay tuned for more…





